
Profound and Detailed
Basis and standard of wireless network security
2022-09-21
With the improvement of wireless security technology, this technology has become the cornerstone of data communication and an integral part of daily life in recent years. It is predicted that most people will soon use their mobile smartphones as their important computer tools. Wireless has become the choice of communication for many people. However, without effective data security, wireless technology will not be developed, and people will still rely on wired networks, despite the cost and other inconvenience.
Data security
What is security? We all have things to protect. In the real world, we have houses and cars; In the digital world, we have personal data, such as social security numbers, online passwords and confidential email exchanges. Industrial and commercial users want to protect their intellectual property rights and products from infringement.
However, we often see that some seemingly safe corporate networks have been attacked by hackers and are helpless. How can we protect our property from theft or infringement? This concern has a long history. Security is based on the fact that we can get our property without hindrance, while others are restricted or cannot access it at all.
In the real world, we lock the door and use the key to open it. In the digital realm, we enter a series of combinations of numbers and letters to enter the computer or obtain data. The basic principle is that there are locks and keys. This metaphor should be kept in mind. The key is unique to the lock; There is no other key to open it. The lock can be removed or destroyed (violent method); Keys may be stolen or borrowed. All security measures have similar weaknesses.
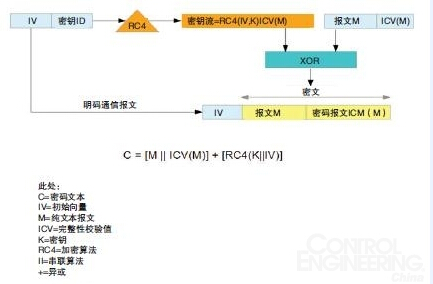
Figure 1: The secret key must match both the client and the access point. Integrate the secret key, including its integrity check value (ICV), and the key stream to encrypt the plain text message. Photo source: Diversified technology service company.
Access control of data
Wireless security can include several different parts, depending on the needs of individuals or companies for security protection. Small systems, such as routers for small offices/home offices or personal wireless local area networks (WLAN), generally restrict access to the network through passwords. Large enterprise WLAN also requires passwords, but requires additional authorization and encryption methods, which rely on the authorization server to control the access to the wireless network. Large enterprises also restrict traffic to different roles, and rely on virtual local area networks (VLANs) and other methods to further subdivide network traffic. These technologies enable administrators to control data and decide who can obtain data based on job responsibilities or department levels.
Wireless intrusion detection system (WIDS) is also used to detect and reduce unauthorized users, and continuously monitor the network; In most cases, these systems are very effective, but the cost is also high. Finally, this point is often ignored. No matter the size of WLAN, there must be a security policy. Most network vulnerabilities are affected by so-called "social engineering". This word describes the process of a person being cheated to show his or her documents to an unauthorized person. A reliable security policy is very effective in educating people how to avoid being cheated or forced to present authorization certificates to unauthorized people.
Development of wireless network security standards
At one time, wireless networks were a bit expensive and new, and were not used in any key applications. Open System Authorization (OSA) is an early method for network access. It is only queried by the access point (AP) to the client to ensure that the client device is compatible with IEEE 802.11. When wired networks are too expensive or impossible to implement, wireless is used as an extension of wired networks. With the wide application of WLAN facilities, it is necessary to develop and implement some way to ensure the security of wireless networks.
The first attempt to ensure wireless network security is the so-called wired equivalent encryption (WEP). The purpose of WEP is to provide an equivalent data reliability verification method for wireless networks, just as it works in wired networks. WEP encrypts plain text with a randomly generated 24 bit "initial vector" (IV) and a 40 or 104 bit static key (for 64 bit or 128 bit WEP, respectively). The secret key must match both the client and the access point.
WEP is subject to its inherent defects, which are related to the construction of keys and the reuse of IV. IV is used to spread plain text, so it is possible to explore the reuse and conflict of IV through various technologies to determine the secret key. Its integrity check value (ICV) is based on the cyclic redundancy check CRC-32, which is not used for safe transmission in essence; This provides another way to explore. WEP can be broken in 10 seconds with common tools; Therefore, WEP is no longer used and should be avoided, even in small office environments.
Temporary Key Integrity Protocol (TKIP) is designed to patch IV reuse issues. Although existing devices are used, TKIP can provide data security because they can be upgraded through firmware upgrade. TKIP is jointly developed by IEEE 802.11i Task Force and Wi Fi Alliance to replace WEP. It has become the basis of Wireless Protected Access (WPA). This is just a transitional measure, a solution provided before more robust security mechanisms are developed and put into use. TKIP uses the only dynamically generated 128 bit encryption key, or "temporary key", while WEP uses a static key. A process called "4-time handshake protocol", which occurs between the access point and the client device, is used to generate these secret keys. Each frame will also be assigned a sequence number; If a frame is received outside the sequence, it will be rejected.
In addition, due to the use of complex keys and the process of developing stronger key streams, the problem of weak keys and key reuse can be solved. TKIP is designed for outdated devices using WEP encryption; RC4 passwords are also used in TKIP. Finally, an enhanced data integrity combination, Message Integrity Coding (MIC), is implemented. Although the use of TKIP is mandatory in WPA, it is optional in WAP2 because WAP2 enforces the use of CCMP-AES encryption.
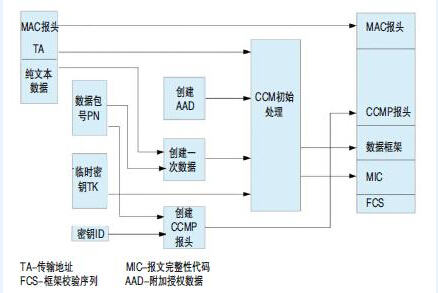
Figure 3: Block diagram of CCMP encryption process. CCMP uses AES group password, which can process data in the group. The encryption method is generally called CCMP/AES
IEEE 802.11 and CCMP/AES
Since realizing that the application of wireless network technology is growing exponentially and that security is essential to support the development of this technology, IEEE 802.11i Working Group has begun to study advanced methods to ensure wireless network security.
Since the IEEE 802.11i Amendment, Robust Secure Network (RSN) and Robust Secure Network Association (RSNA) have been introduced to provide a framework for secure wireless networks. Generally speaking, successful authorization means that both parties of the transaction have verified each other's identities and have generated dynamic encryption keys to ensure the transmission of secure data.
WPA2 is a complex security method, which draws on the advanced encryption method provided by the United States Federal Information Processing Standard (FIPS-197). The name of WPA/WPA2 was developed by the Wi Fi Alliance, which mirrors the copyright of IEEE Standard Control Engineering Network. It is actually a kind of authentication to ensure that devices can follow a common security standard. WPA2 specifies two types of security: password authorization control engineering network copyright for small and small office/home office networks, and 802.1X/EAP security for enterprise networks.
WPA2 forces the use of a new protocol, Counter Mode and Ciphertext Block Link Message Authentication Code Protocol (CCMP). CCMP uses AES block password; Replace RC4 password and temporary key integrity protocol used in WEP. Block ciphers process data in data blocks, while data stream ciphers, such as RC4, are bit by bit encrypted in the form of serial data streams. This encryption method is generally called CCMP/AES. CAES uses 128 bit keys to encrypt 128 bit data sets. CCMP/AES has made many improvements, including temporary key (TK), packet encoding, one-time data (numbers or bit strings used only once), upper layer encryption, and additional authorization data (AAD). It should be understood that AES is a standard rather than a protocol. AES standard specifies the use of Rijndael symmetric block cipher, which can use 128, 192, and 256 bit keys to encrypt 128 bit data groups.
CCMP is a security protocol. It follows a carefully designed procedure, which includes encrypting sensitive data using the algorithm specified by AES. The CCMP consists of specialized components that can provide specific functions. It also uses a temporary key to complete all encryption and data integrity processes.
Five Skills of Defense in Depth Strategy
Advanced network security and system monitoring functions can improve power reliability and reduce energy consumption. Allowing network access has caused industrial enterprises to worry about network security, and defense measures in depth will help.
In order to make a decision on intelligent power management, in order to reduce energy consumption and improve power reliability, it is very important to monitor and understand how power is used, although collecting and obtaining this information will cause people to pay attention to network security. The monitoring function realized by the industrial control system can be used to obtain the information of the equipment, so as to avoid shutdown and understand the system parameters and diagnostic information, but at the same time, it will also cause a new risk: access to unauthorized information, or provide unauthorized users with the opportunity to unconsciously access the equipment operation and parameter settings.
"Defense in depth" is a strategy to establish different barriers at multiple levels within an organization to ensure the safety of industrial control systems. The five techniques for "defense in depth" include:
1. Establish a firewall for communication between multiple network segments and regions in the industrial control system network in order to add more strict multiple rules;
2. By grouping the key components and isolating them from the traditional commercial IT network, an uncontrolled zone is established in the established firewall;
3. Deploy intrusion detection and prevention systems, and focus on identifying possible incidents in the industrial control system network;
4. Establish good review policies, processes, standards and guidelines for the security of industrial control networks, and record them in text;
5. Continuously carry out safety assessment and training to ensure the safety of industrial control systems and the safety of people relying on these industrial control systems.
(Author: Daniel E. Capano)
<< Previous page
Next page >>